One of the more common things you will read about nowadays in healthcare news portals is how another hospital or organization has suffered from a data breach. Whenever patient information is involved, these become HIPAA breach examples. The compromised information is known as PHI (protected health information) in HIPAA terms and that is what HIPAA primarily aims to safeguard. HIPAA breaches consist of unauthorized access or disclosure of PHI and these are either caused by hackers, inadvertent employees, or individuals with malicious intent. While these are undesirable, organizations dealing with PHI can learn from them to enhance their security measures.
Let’s look at some of the recent HIPAA breach examples.
Compromised email account
Oregon-based Santa Rosa & Rohnert Park Oral Surgery recently detected that an outsider accessed one of its employee’s email accounts without authorization. Upon investigation, it was found that the account was compromised since December 20th, 2019, and was in the same state until March 11th, 2020 – until the account was secured the same day they detected the anomaly. It contained PHI which has potentially been stolen or at least accessed by the hacker.
The healthcare provider is currently ensuring that security measures are being enhanced so that such an incident does not repeat itself. The number of affected individuals or the PHI compromised were not disclosed by the provider as of yet.
MNS’s breach affected over 30,000
Ohio-based Management and Network Services (MNS) provides support services to hospitals. It recently discovered that some of its employees’ email accounts have experienced unauthorized access.
MNS learned of this potential breach around August 21st, 2019. Several of its employees’ email accounts were accessed by unauthorized parties between April and July 2019. MNS launched an investigation, and upon analysis, it found that five of the compromised email accounts contained PHI. The information contained, but was not limited to, names, treatment information, diagnosis, medications, DOB, and Social Security numbers. Also, it varied from person to person. The HIPAA breach affected over 30,000 individuals.
MNS will be enhancing email security by using complex passwords and MFA (multi-factor authentication). Safe to say, training will be required to ensure that all these security enhancements will be made effectively.
ACMC accidentally exposed PHI of over 3,600 individuals
Another Ohio-based provider on the list, Ashtabula County Medical Center (ACMC) experienced an incident that partially compromised 3,683 patients’ information. The difference with the other breaches is that this time, it happened internally, and was a mistake. While complying with government regulations, it posted a spreadsheet online on January 6th, 2020. On March 12th, 2020, it learned that the document, unfortunately, contained partial PHI of 3,683 individuals – names, treatment and medical histories, and diagnoses were part of it.
ACMC updated its policies as well as security measures accordingly to ensure that such an event is not repeated in the future.
What to learn from these HIPAA breach examples
The first thing to notice is that HIPAA breaches happen all the time and can hit you even at the most unexpected times. Thus, organizations have to be prepared all the time for worst-case scenarios instead of thinking that they will never face a breach. They need to have guidelines prepared for what to do before, during, and after a breach.
Secondly, these do not have to be external breaches where cybercriminals just gain access to the email accounts and steal the data or load the devices with ransomware demanding money. As the last example showed, breaches can occur internally too. There are many cases where hospital staff members are found snooping on medical records without any valid reason – most of them lose their jobs because of doing so. In other cases, such disclosures happen inadvertently when not enough attention is paid to ensuring the security of PHI.
Thirdly, HIPAA breaches can be quite costly and complicated. The common things about all data breaches involving PHI are:
- Detecting the anomaly
- Launching an investigation
- Coming up with a summary
- Notifying individuals as per the HIPAA Breach Notification Rule
- Compensating patients with complementary services
- Implementing additional security measures
All of these can be quite expensive and time-consuming. Moreover, it affects the goodwill of the affected organization. All of these should be avoided by following the HIPAA rules and regulations to the T right off the bat. That can be done by ensuring HIPAA compliance.
However, there is an issue. One common misconception about HIPAA is that many think that HIPAA compliance needs to be done once – that’s the biggest mistake. HIPAA compliance is a continuous process since all the regulations keep changing, and you need to ensure it at all times. If you become HIPAA compliant once, that means that you are ensuring compliance with the rules and regulations up to that point – what about the new changes? What about new threats? Thus, ensuring compliance continuously is the only way to stay safe.
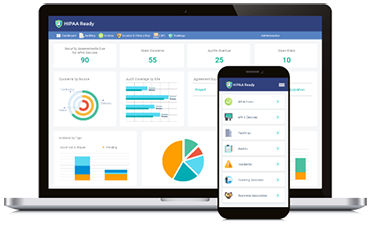
Ensure HIPAA compliance with HIPAA Ready
HIPAA compliance is an arduous, continuous, and complex process – and that is an understatement. However, you can simplify compliance with HIPAA Ready – a robust HIPAA compliance software. Ensure proper training management so that your employees do not accidentally disclose or access patient data, keep all HIPAA-related information in a centralized location so that everyone can stay on the same page, and conduct internal audits to detect vulnerabilities and fix them. HIPAA Ready has been made to reduce the administrative burden, simplify and streamline compliance management, and to make sure you are continuously complying with HIPAA regulations.